场景简介
传统 IAM 在内部员工管理和外部用户管理等场景中力不从心;上线新应用和兼容老应用时不够灵活。与此同时,横空出世的 IDaaS 服务由于兼具云的扩展性优势和跨环境的身份识别及权限管理能力,取代了传统的 IAM 成为企业基础设施。
Authing 的价值
IDaaS 是 Identity as a Service 的缩写, 包含传统 IAM 的全部功能,并能为企业带来更多收益:提升营销和运营效率;加速新业务上线;提升安全性降低网络攻击风险;提升用户体验。
运营能力提升
传统 IAM 账号中心的运营能力较弱,难以满足大型组织在业务方面的需求,而 IDaaS 的多租户运营平台和自动化工作流(Workflow)则可以便捷地提升企业运营效率。

Authing 如何支持各种场景
API 安全
在零信任环境中提高 API 安全性并确保内部和外部合作伙伴用例的合规性可能非常具有挑战性。Authing 基于开放标准的方法提供端到端的 API 安全和管理。
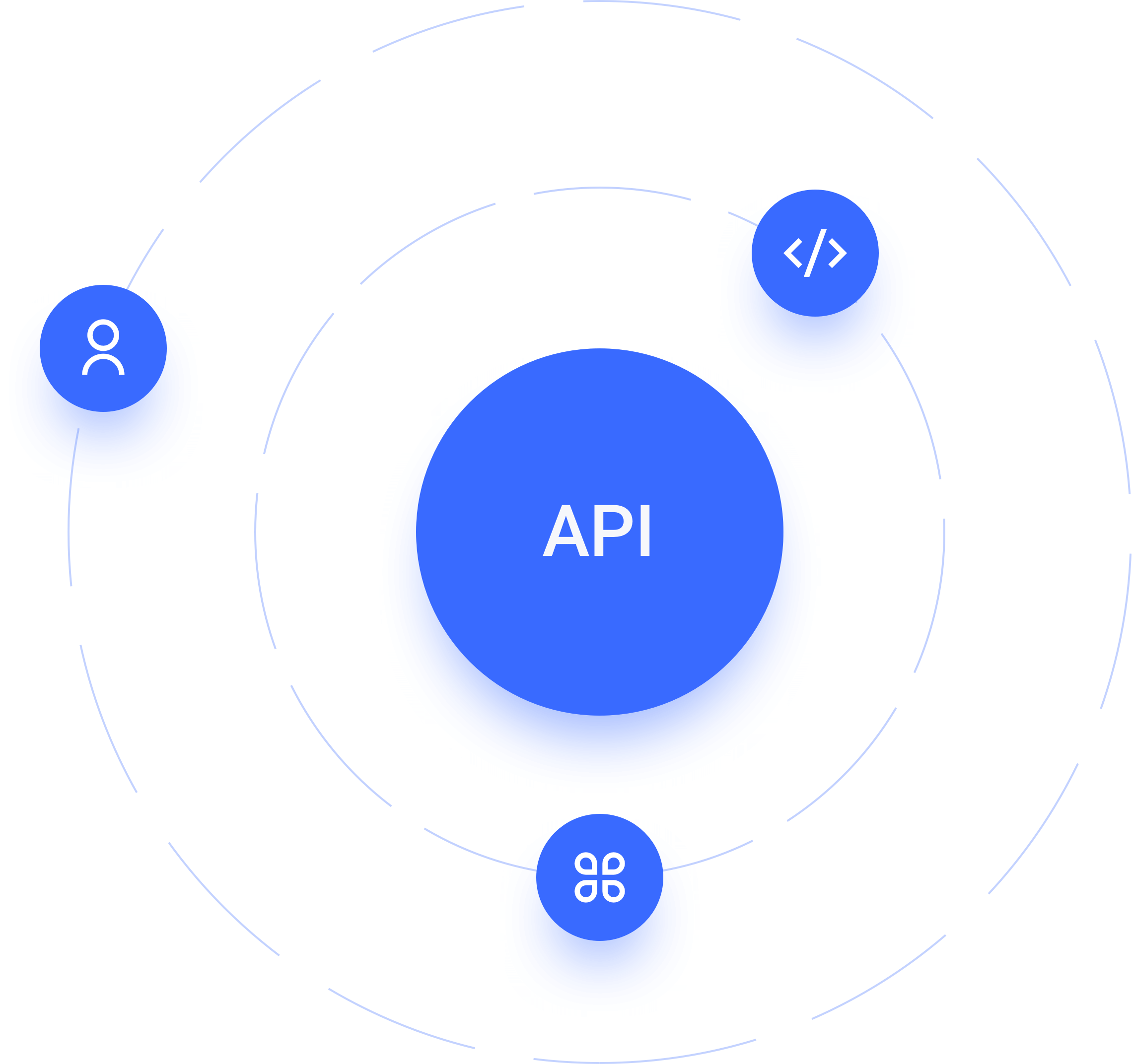
对于用户
通过支持所有 OAuth 2.0 授权流以及细粒度的范围和权限,轻松保护和公开您的 API,从而扩大市场范围并提供更好的用户体验。
对于应用和系统
只需轻按一下开关,即可轻松促进 API 与非交互式外部客户端以及内部 API 之间的安全通信。
对于企业开发者
使第三方应用服务器、API 和系统后端能够向您的 API 发出经过身份验证的请求,同时始终保持对精细范围和权限的控制。
众多合规认证,保障身份安全

毋庸置疑,客户数据安全性和合规性是大多数公司的首要考虑因素。Authing 在产品中内置了先进的安全性,因此您无需为您的用户和业务安全忧虑。
行业标准协议:通过采用支持 OAuth 和 OpenID Connect 等行业认证标准的身份平台,提高业务运营和执行的一致性和连续性。
合规性和认证:Authing 拥有多项国内国际合规认证,包括国家三级等保、SOC 2、GDPR、ISO 9001、CCPA、PCI、HIPAA 和 FERPA 等,誓要保障每一位用户、每一个业务的安全。
公共和私有云:在 Authing 的公共云、我们的私有云或您的 AWS 环境中托管您的应用。我们高度可用的多租户云服务每天可以处理大量交易。
快速集成 五分钟实现
单点登录、认证授权、权限管理等功能